Unable to Add This Agent Correct Any Errors Below and Try Again Ldap
Initial troubleshooting steps
-
Go to the Troubleshooting tab in the Admin Console to view the logs for the Ad/LDAP Connector:
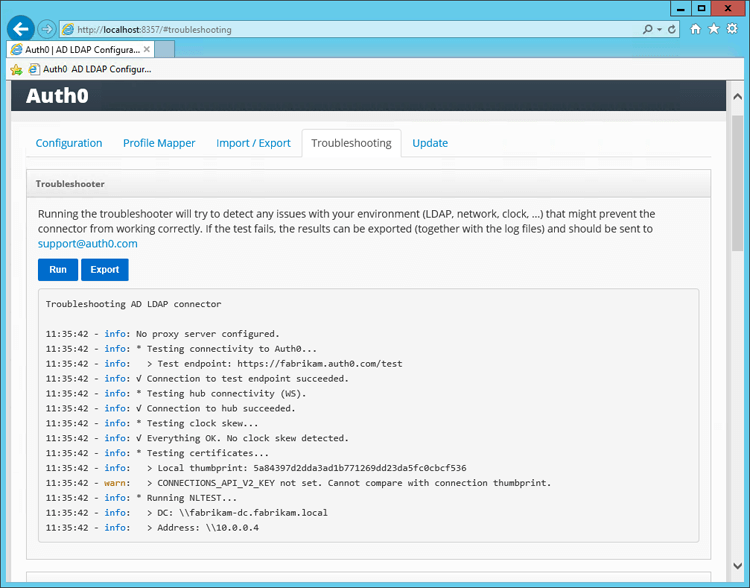
-
Click Run on the Troubleshooting page to run the troubleshooting tool to detect the virtually common problems related to the Ad/LDAP Connector. To detect bug with certificates prepare
CONNECTIONS_API_V2_KEYin theconfig.jsonfile.Y'all can as well launch exterior of the Admin Console:
-
Windows: C:\Programme Files (x86)\Auth0\AD LDAP Connector\troubleshoot.cmd
-
Linux: node troubleshoot.js
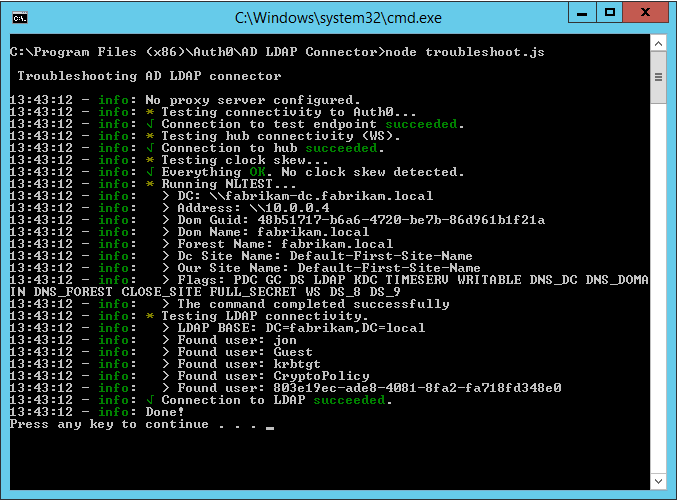
To learn more than, see Advertizing/LDAP Connector Configuration File Schema.
-
-
Run across the listing of mutual bug and solutions below.
Installation and configuration issues
After clicking Save, the AD/LDAP Connector configuration console performs a series of tests to validate the entered data. The results of the tests are displayed nether the Configuration log heading in the console screen. An explanation is provided beneath of the tests performed.
-
Exam 1: Attempts to establish a TCP connection to the LDAP server and port specified. If Test one fails, check basic network connectivity and firewall settings that might prevent such a connection.
-
Examination ii: Attempts to perform an LDAP bind on the LDAP server and port specified and with the username and password provided. If Exam 2 fails, cheque the LDAP connectedness string, search path, username, and countersign.
-
Exam iii: Attempts to perform an LDAP search against the directory to check the privileges of the specified username. If Test iii fails, check the privileges of the username in the target directory.
-
Test 4: Attempts to found a connection to the Auth0 server. If Examination 4 fails, cheque network connectivity and firewall settings that might forbid such a connexion.
Common issues and solutions
Clock skew
The connector requires the clock on the server to exist synchronized with the Auth0 service. The maximum allowed threshold is v seconds.
If you take a clock skew, you lot'll see output like this in the troubleshooter and connector logs:
12:18:55 - info: * Testing clock skew... 12:18:55 - error: × Clock skew detected: 12:eighteen:55 - error: > Local time: 2020-05-04 12:18:55 12:eighteen:55 - fault: > Auth0 fourth dimension: 2020-05-04 12:19:10 Brand certain the clock of your server is current. If the fourth dimension is not correct, information technology will cause authentication requests to neglect. This can be fixed past ensuring the organization is properly configured to poll a sync server via the Network Time Protocol (NTP). In Windows environments, the NTP provider is usually the aforementioned domain controller. Brand sure that your Domain Controller is synchronized with some external service.
For instructions on synchronizing your Active Directory surroundings with an external time server, bank check out this blog post: How to configure NTP server in Active Directory, Pace by footstep.
If y'all are unsure if your server'due south clock is in sync with NTP, goto https://nist.time.gov/ and compare the fourth dimension on that page with the fourth dimension in the server where the connector is running. You shouldn't notice more than than a 1 2nd difference between them.
No connexion to Active Directory
The connector should be installed on a server that can reach the LDAP server. When firewalls and VPN connections are placed between the Ad/LDAP Connector and the LDAP server it may lead to connectivity issues.
-
In a Windows Network with Active Directory employ the
nltestcommand. To test if a specific automobile can reach thefabrikam.localdomain, applynltest /dsgetdc:fabrikam.local. -
To see to which domain the current server is connected use
nltest /dsgetdc:. -
When the domain does not be or is unreachable,
nltestwill render an error message:Getting DC name failed: Status = 1355 0x54b ERROR_NO_SUCH_DOMAIN
UNABLE_TO_VERIFY_LEAF_SIGNATURE error message (Private Cloud)
This error applies to the Advert/LDAP Connector in combination with Private Deject.
This error message occurs when the Connector fails to commencement when it can't validate the SSL certificate configured in the Private Cloud. This can happen when the Root Certificate (or any Intermediate Certificates) are missing in the machine'south Document Shop (Windows). In social club to solve this, import the certificate chain in the Local Auto > Trusted Root certificate store on the automobile where the Ad/LDAP Connector is installed.
Connector behind a proxy
-
If the automobile hosting the connector is backside a proxy, you can configure an
HTTP_PROXYsystem environment variable pointing to the URL of your proxy, or yous can fix this variable in theconfig.jsonfile in the connector installation directory. If using an authenticated proxy, the URL must be in the formathttp://USERNAME:PASSWORD@SERVER_URL:PORT. -
Changing the
config.jsonfile or setting environment variables requires restarting the Connector service for the changes to take event. -
The
HTTP_PROXYURL cannot point to a .pac (motorcar-config) file; it must exist the URL of the proxy itself. If your proxy is configured through a .pac file, download the .pac file and notice the proxy URL there. -
An incorrectly configured proxy can result in several issues, such equally:
-
-
Auth0 servers not reachable
-
SELF_SIGNED_CERT_IN_CHAINerrors
-
-
If yous have configured a proxy URL and restarted the connector service but are however seeing
SELF_SIGNED_CERT_IN_CHAINerrors, make sure that your server is trusting the root certificate of the proxy. On Windows servers, you can check this by openingcertmgr.mscand looking for your proxy's document. To learn more, see the article Proxy auto config (PAC) on Wikipedia.
No internet connectivity
https://YOUR_DOMAIN should be reachable from the server. A quick test for this is to open a browser pointing to https://YOUR_DOMAIN/test.
Service business relationship permissions
The Service account used to configure the connector must have read permissions on the AD/LDAP server, every bit well as capable of querying groups for users.
Kerberos problems
To enable verbose logging of Kerberos requests, add together a organisation level environment variable DEBUG=kerberos-server. So restart the Connector. Try logging in over again, and check the logs for more information.
If yous have Kerberos enabled, but your users are being prompt for username/password, you lot likely don't have the IP address setting properly configured.
For more information on using Kerberos, see Configure AD/LDAP Connector Hallmark with Kerberos.
The Connector uses two levels of configurable caching:
-
Ane on the Auth0 server, which caches both credentials and user profile.
-
A second level in the connector itself, which only caches group membership of a user.
The server caches the concluding successfully authenticated user profile, including the username and countersign (hash). It is enabled by default, and can exist disabled. The purpose of this get-go level cache is to maximize availability of authentication transactions when Ad is unavailable (such equally a network outage). Information technology is just activated if the Connector/Advert/LDAP servers are unavailable.
The Connector caches only groups a user might be a member of. Its lifetime is controlled with the GROUPS_CACHE_SECONDS configuration variable. If non present, the value is 600 seconds. Groups are buried, because by default, the Connector retrieves all group membership of a user recursively, which can exist plush in some AD/LDAP installations. Cache is deleted on each Connector restart.
These two settings might affect how profile information flows to an app. But in full general, Advertisement changes don't happen very often.
In some AD/LDAP installations, user attributes synchronization takes a few minutes.
Connector restarts after "auth0: Connection closed." message in the log
To avert the requirement of an open up inbound port in your servers, the Connector creates a websocket connection to an available node in Auth0's server cluster and keeps it open to heed to incoming letters from Auth0.
Approximately once a mean solar day (though this frequency might vary under certain circumstances) each server node will cease the connection to allow internal deployment processes to occur. The Connector will detect the closed connection and terminate the procedure, allowing the service stack to restart the procedure, create a new connection to an available node and resume operations. To avoid any downtime, enable the cache:
-
Navigate to Auth0 Dashboard > Authentication > Enterprise, and select the Active Directory/LDAP connection blazon.
-
Select the name of the Advertizing/LDAP connexion to view.
-
Go to the Applications view, and enable the connection for the advisable application(due south).
-
Select Save.
Receive "postUrl is required" fault
This is usually thrown if additional configuration for custom domains have not been fabricated. In guild to apply Advertisement/LDAP connections with Kerberos back up, yous will need to update the Ticket endpoint to work with the custom domain.
-
Modify the Connector configuration file with the
PROVISIONING_TICKETvalue changed to utilize your custom domain in the formathttps://<YOUR-CUSTOM-DOMAIN>/p/advertising/jUG0dN0R. -
Restart the AD/LDAP Connector service for the modify to have effect.
Contact Auth0 Support
If y'all have not been able to resolve your bug contact Auth0 Support.
-
Click Export to create a .zip file containing the
config.jsonfile, thelib\\profileMapper.jsfile, thecertsfolder and the output of the troubleshooting tool. -
Open a back up ticket if y'all're experiencing problems with the following information:
-
Symptoms
-
Advert/LDAP Connector version
-
The .naught file containing: Windows:
C:\Program Files (x86)\Auth0\AD LDAP Connector\config.jsonLinux:/opt/auth0-adldap/config.json -
The service log files from: Windows:
C:\Plan Files (x86)\Auth0\AD LDAP Connector\logs.logLinux:/var/log/auth0-adldap.log
-
Acquire more than
- AD/LDAP Connector System Requirements
- Import and Consign AD/LDAP Connector Configurations
- Set Up Advert/LDAP Connector Test Surround
- Update AD/LDAP Connectors
- AD/LDAP Connector Configuration File Schema
- Monitor Ad/LDAP Connector with Organisation Heart Operations Director
Source: https://auth0.com/docs/extensions/ad-ldap-connector/troubleshoot-ad-ldap-connector
0 Response to "Unable to Add This Agent Correct Any Errors Below and Try Again Ldap"
Post a Comment